Web Application Security: Vulnerabilities, Definition, Testing, Tools, and Ethics
Web application security is the process of keeping your website secure from vulnerabilities and malicious attacks. With so many people relying on web applications, it is increasingly vital to keep them safe. This article will answer some of the most common questions about web application security like what are the most common vulnerabilities on websites, methods to find out whether your website has any vulnerabilities, and how do you fix them once they’ve been found? Let’s dig in!
What Are The Most Common Web Application Vulnerabilities?
Web application vulnerabilities refer to security loopholes in the web application that can allow a hacker to gain access to your website. This is extremely dangerous because once they have gained access, hackers can cause real damage by deleting or modifying data and stealing sensitive information such as usernames and passwords.
Among the different types of web application vulnerabilities, the most common ones are:
- Insecure coding practices
- Cross-site scripting (XSS)
- Injection flaws
- Insufficient logging and monitoring
- SQL injection
- Forgotten password resets
- Brute force attacks
- Improper access control
- Insufficient Transport Layer Protection (not using SSL/TLS when it should be used).
- Authentication bypass
- Session ID transmission over SSL/TLS channels
Now that we’ve discussed the most common vulnerabilities web applications face, let us check out how to find out whether your websites have any vulnerabilities.
How To Find Out Whether Your Website Has Any Vulnerabilities?
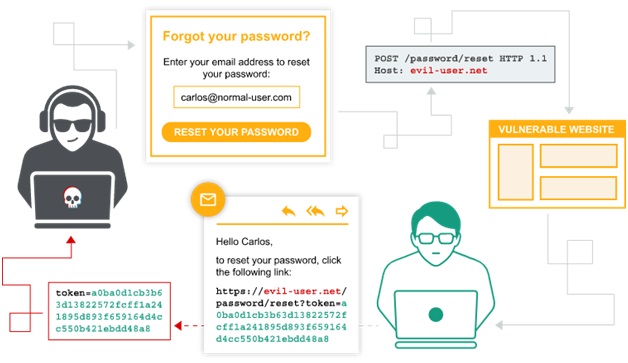
One of the best ways to determine if your web application has any vulnerabilities is by conducting a online penetration testing or security audit.
A penetration test, also known as “pentesting“, consists of an authorized attempted intrusion into your network with the goal of exposing security weaknesses. This can be done manually or by making use of automated tools.
Once the vulnerabilities have been found, take actionable steps to fix them and here, a security audit comes in handy.
A security audit is an in-depth review of your systems and networks that looks for potential vulnerabilities as well as deficiencies in security policies, procedures, and practices. This is a great way to make sure your systems are secure before they fall victim to an attack, which can lead to significant financial loss for your organization.
Web Application Security Testing – What Is It and Why Is It Important?
A web application security test or penetration test is a type of vulnerability assessment that examines the network, systems, and applications to uncover any potential risks.
Web application security testing is important because it will uncover any loopholes in your system or network that a hacker can exploit. It is also vital because it helps you protect against cyber attacks and data breaches, which could potentially cripple your business.
You can conduct these tests yourself using automated online tools. However, it’s important to realize there are ethical and legal implications involved when you attempt this on your own. For example: if someone were able to infiltrate an application without authorization after completing one of our free web application security scanners then they could be charged with criminal acts such as breaking into computer networks. With all of this in mind, it’s recommended that anyone considering conducting their penetration testing contact an attorney who specializes in cyber-security first.
How To Conduct A Web Application Security Testing?
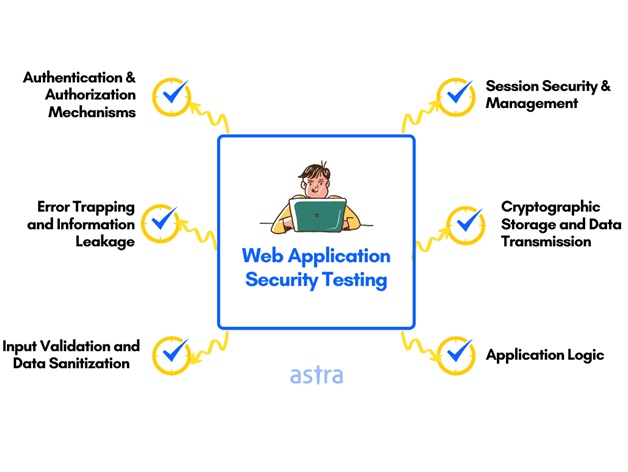
The first thing you’ll need to do is determine what needs to be tested, the tools and techniques that should be used, as well as who will conduct the testing (internal or external). Once your initial tests are complete, it’s important to review them with an expert in order to identify any potential issues missed by automated scanning tools. Some of these experts include Penetration testers, Information risk assessors, Compliance auditors IT/systems administrators, Network Administrators. Depending on your organization there may also be additional compliance audits required for PCI DSS & HIPAA if they apply so make sure everyone involved understands what is required.
Since there is no one-size-fits-all answer to this question, the best way to test an application will vary depending on the specific situation. However, here are some general steps to take during web application security test:
- Identify the most common application vulnerabilities.
- Prioritize your testing based on risk.
- Gather information about the organization that will be using the web app.
- Use a combination of automated & manual tools to conduct an in-depth security test.
Determining what vulnerabilities your website might be susceptible to via research of common threats against similar applications is crucial. Your test plan should include each relevant area where threats could occur. Here are just a few examples of areas worth considering when developing your pen-testing methodology:
- Authentication controls
- Post request manipulation
- Data access components
- Authorization controls
- Session management and authentication controls
- Application back-end processing (data validation)
This is just a general overview, so you’ll want to work with experts to create a testing plan that is tailored specifically for your organization.
Tools For Web Application Security Testing
Many tools are readily available to help with web application security testing. For example, you can use automated scanners to perform a quick assessment of your website’s public-facing areas to find vulnerabilities. Here are some of the more popular tools:
- Astra Pentest
A comprehensive web app security testing tool that offers manual and automated vulnerability scanning as well as vulnerability management to discover and fix vulnerabilities in your application efficiently.
- Acunetix Web Vulnerability Scanner
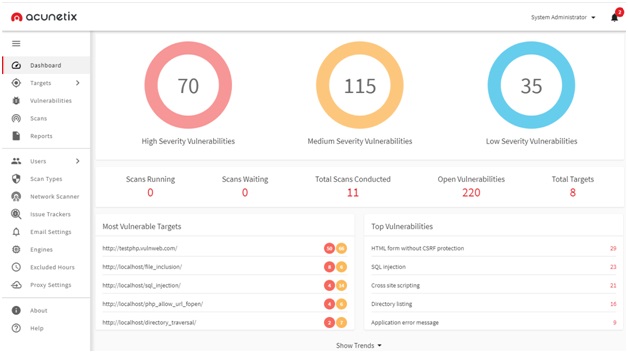
This scanner can identify a wide range of vulnerabilities, including SQL injection and Cross-site scripting.
- OWASP ZAP
This is an open-source security tool that can be used to test the security of web apps. Web application security testing with OWASP ZAP is easy, free, and simple to use making it a great option for beginners.
- OWASP Xenotix XSS Exploit Framework – This scanner identifies vulnerabilities in .NET and Java applications.
- Burp Suite – This is a popular tool for intercepting and manipulating web traffic. Web application security testing with Burp Suite is a comprehensive option as it includes both a scanner and a proxy server.
- Nessus – This is an automated scanner that can help organizations identify vulnerabilities and misconfigurations.
These tools can be used to identify a huge range of vulnerabilities like SQL injection, broken authentication, and more. However, they are not perfect and sometimes require manual intervention in order to get the most accurate results. That’s why it’s important to have a team of experts who can review the findings and help you fix any vulnerabilities that are discovered.
Legal & Ethical Implications of Web Application Security Testing
As mentioned earlier, there are legal and ethical implications to consider when performing a web application security test. It’s important to be aware of these before starting your assessment so that everyone involved understands the risks and consequences.
One of the biggest concerns is unauthorized access to confidential data. If you gain access to information that you’re not authorized to see, you could be in trouble with the law. Some might even result in you facing criminal charges.
Another consideration is damage done to systems or data as a result of your testing. If you intentionally cause damage, you could be held liable for the costs associated with repairing or replacing the damaged items.
It’s also essential to remember that not all vulnerabilities are created equal. Some may have a low risk of being exploited, while others pose a high risk. You need to weigh the risks and benefits of exposing each vulnerability before deciding whether or not to disclose it.
Conclusion
So there you have it – a quick overview of the most common web application vulnerabilities, how to find out if your website has any vulnerabilities, how to conduct web application security testing, and the tools for it. Along with this the article also discusses the ethics and legality surrounding a web application security test. We hope this information will help you keep your systems safe from attack and protect your data. Stay vigilant!